Report - Paper 'P2PWNED: Modeling and Evaluating the Resilience of Peer-to-Peer Botnets' accepted at IEEE S&P 2013
|
An increasingly popular way chosen by botmasters to increase botnet resilience is to organize the botnet as a Peer-to-Peer (P2P) network. In a P2P botnet, bots connect to other bots to exchange C&C traffic, eliminating the need for centralized servers. As a result, P2P botnets cannot be disrupted using the traditional approach of attacking critical centralized infrastructure. The following figure shows the history of P2P botnets. 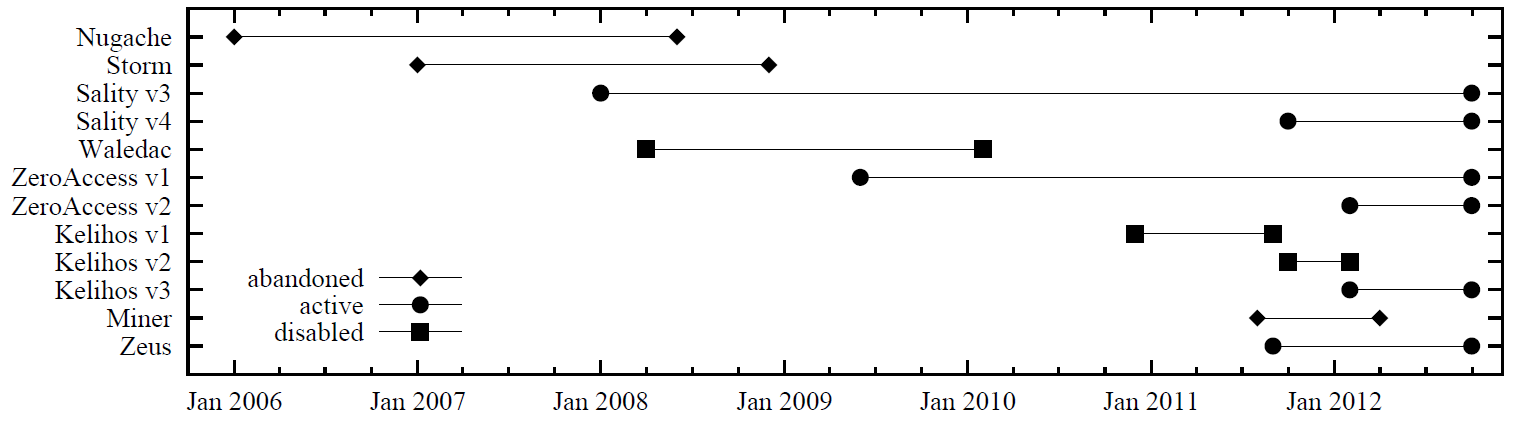
To spy on these botnets, we modeled reconnaissance methods and evaluated the resilience of current P2P botnets to these methods. That is, we evaluated to what extent the P2P botnets are able to deter malware analysts from enumerating the bots in the network. Luckily, all current P2P botnets can be enumerate quite easily. In general, we distinguish between botnet families, botnet variants and botnets. We use the term botnet family to denote a specific strain of a botnet. The term botnet variant is used to denote a variant within a botnet family. Finally, we use the term botnet to refer to a coherent collection of hosts infected with a specific botnet variant. Some botnet variants contain several disjoint botnets. The following figure shows each of the P2P botnet variants that are still active as of writing this. 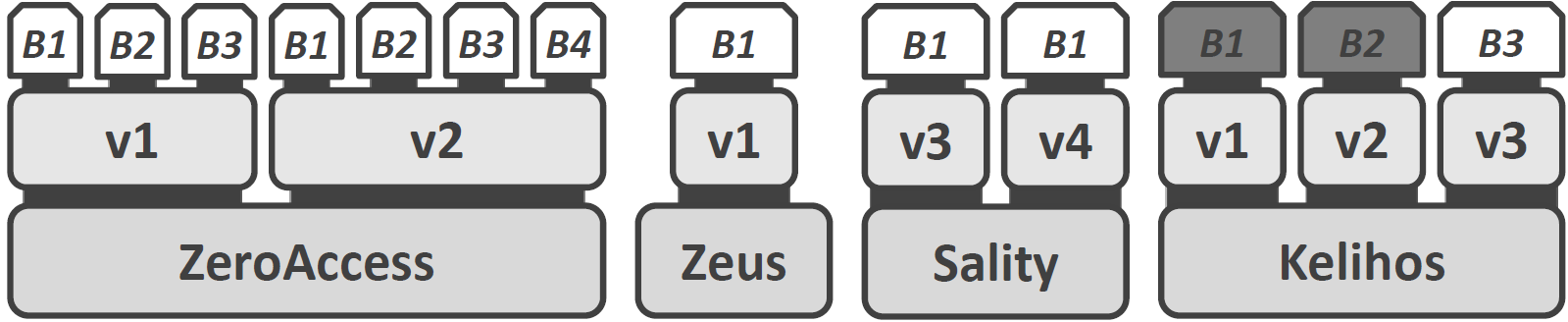
As a potential countermeasure against these P2P botnet variants, we formalize attacks that can be used to disrupt P2P botnets. Examples of such attacks include sinkholing, where all bots are redirected to an attacker-controlled machine called a sinkhole, and partitioning, which aims to split a botnet into unusable sub-networks. Similarly, we modeled reconnaissance methods and evaluated to what extent the P2P botnets are able to deter malware analysts from enumerating the bots in the network. Luckily, all current P2P botnets can be enumerate quite easily. I am happy to present our work at IEEE S&P in San Francisco, May 19-22, 2013.
Yours
|

