Report - Paper on Exploit-as-a-Service at CCS 2012
In order to understand the impact of the exploit-as-a-service
paradigm on the malware ecosystem, we perform a detailed analysis
of the prevalence of exploit kits, the families of malware installed
upon a successful exploit, and the volume of traffic that malicious
web sites receive. To carry out this study, we analyze 77,000
malicious URLs received from Google Safe Browsing, along with
a crowd-sourced feed of blacklisted URLs known to direct to exploit
kits. These URLs led to over 10,000 distinct binaries, which
we ran in a contained environment.
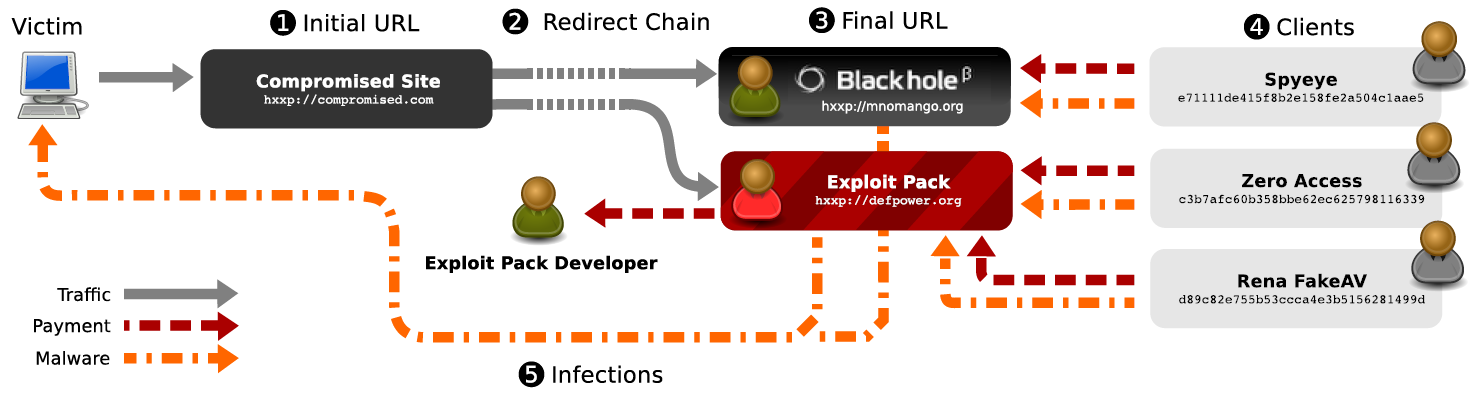
Our results show that many of the most prominent families of malware now propagate through driveby downloads - 32 families in all. Their activities are supported by a handful of exploit kits, with Blackhole accounting for 29% of all malicious URLs in our data, followed in popularity by Incognito.We use DNS traffic from real networks to provide a unique perspective on the popularity of malware families based on the frequency that their binaries are installed by drivebys, as well as the lifetime and popularity of domains funneling users to exploits. I'd like to thank Chris Grier for the terrific job he has done to get all us authors contribute to such a great paper! Also thanks a lot for giving the presentation at CCS 2012.
Yours
|

